When a user at home types www.google.com in browser, what protocol and data packets are involved in the process?
When a user at home types www.google.com in browser, what protocol and data packets are involved in the process?
GPRS Tunneling Protocol (GTP) is a group of IP-based mobile communication protocols defined by 3GPP used across various interfaces in roaming, RAN, and within the packet core of 3G and 4G networks to carry GPRS traffic over GSM (2G), UMTS (3G), LTE (4G), and 5G NR radio networks.
Why I Choose n8n? I’m building an all-in-one automation solution that integrates multiple third-party application into a cohensive system.First, it fetches real-time news through APIs, then processes this information using AI to analyze my preferences and behavior, delivering personalized recommendations. These insights are automatically organized and inserted into Notion at scheduled time. Finally the system shares key takeaways with my Slack community.
❌ use any cloud instance / VPS server
❌ domain name
🆓 for whole project
Since n8n cloud only have 14 days free trail, so I try to selfhost my project. There are two choices: npm or docker. Here’s I will use docker to build. That is based on your preference. For me, I fed up with node related package.
Follow steps in here
1 | docker volume create n8n_data |
Lovable is a no-code AI-powered tool for generating websites, with the option to transfer project to github, update the code locally and integrate to your database instead of using their preferred choice: supabase. I’m currently using it to redesign the UI of my side project, Spendwise(Tech stack:Flask+SQL+RabbitMQ), aiming to improve the design and explore additional functional features. I’m using the free version of Lovable, which allows up to 5 queries per day which means we should cherish every chance of asking question. My side project github repo SpendWise.
CyberSecurity covering prevention, detection, response, and risk management. It involves implementing security policies AAA(authentication, authorization, accountability), controls, and frameworks to ensure the (CIA triad)confidentiality, integrity, and availability of data and networks, while preventing DAD(discloure, alteration, and denial)
unauthorized access, compromise, destruction or denial of access.
While working on a Grafana dashboard that connects to SQL, I used SQL queries and implemented test automation to simulate user input, modify/lookup the database and verify expected results. This blog post documents my knowledge of SQL. I will use https://www.sql-practice.com/ patient system as my part of query data, you can try it by yourself.
When a user at home types www.google.com in browser, what protocol and data packets are involved in the process?
Communication between difference devices must go through this OSI models. Each layer in OSI model has a specific role, from physical data transmission (Layer 1) to application-level interactions (Layer 7). In this blog, we’ll explore the purpose of each layer, with a deep dive into Layer 7 (Application Layer)—the layer closest to end users. Future posts will cover the remaining layers in detail.
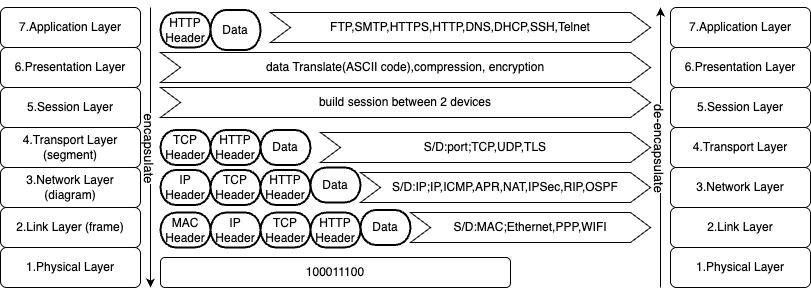
Networking enables communication by forwarding data through interconnected devices (hops) until it reaches its destination. A crucial step in this process is defining routing protocols, which can be either:
Static Routing (manually configured routes)
Dynamic Routing (automatically adapting to network changes): RIP, OSPF, BGP