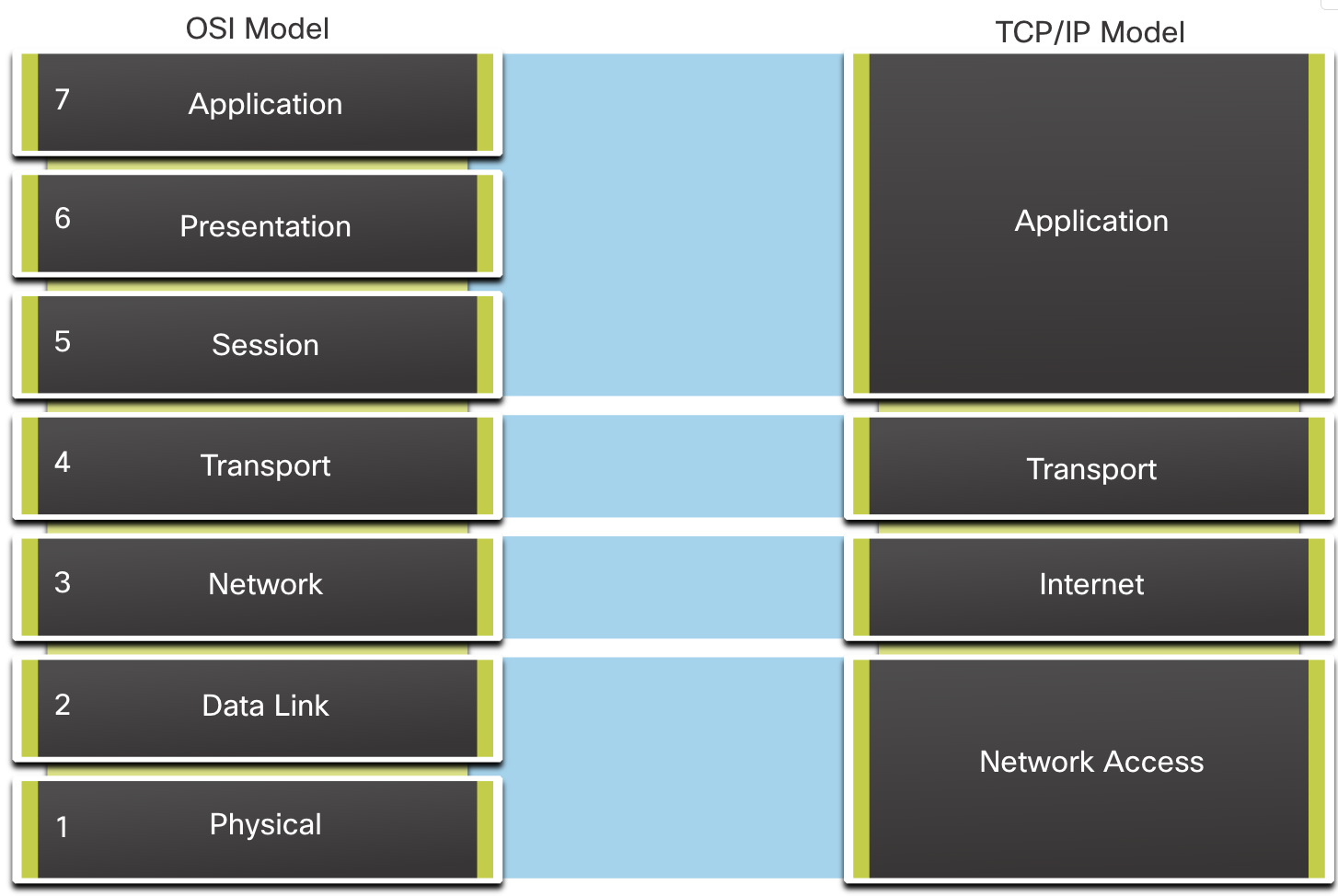
Communication between difference devices must go through this OSI models. Each layer in OSI model has a specific role, from physical data transmission (Layer 1) to application-level interactions (Layer 7). In this blog, we’ll explore the purpose of each layer, with a deep dive into Layer 7 (Application Layer)—the layer closest to end users. Future posts will cover the remaining layers in detail.
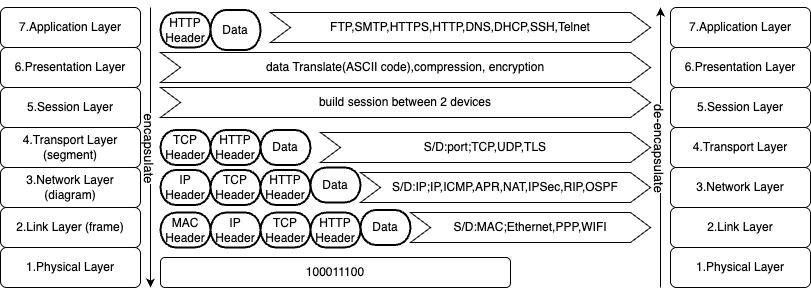
Layer7: Application layer
FTP
Port: 20/21, 20 for data,21 for control
use TCP
controlplane work on port 21, dataplane work on port 20. Controlplane setup connection; dataplane have two modes: active mode and passive mode. If the server initializes the 3-way handshake, it is active mode; if the client initializes 3-way handshake, it is passive mode. FTP won’t encrypt data, if you send sensitive data you should choose SFTP, port 22 which is an SSH port as well.
FTP workflow
Active Mode:
- step: client(192.168.1.100) connects to server(203.0.113.1) at port 21 to setup controlplane connection
- step: client send PORT command(IP address, port number) to server
- step: server initialize data connection, then file transfer
Passive Mode:
- step: client connects to server at port 21 to setup controlplane connection
- step: client send PASV command(IP address, port number) to server
- step: server responses with port dynamically choose:3000
- step: client initialize data connection
Passive mode is more common when client-side firewall/NAT
SSH
Port: 22
use TCP
securely remote access, SFTP built on top of SSH. use key pair/password to access
HTTP/HTTPS
Port: 80 for http,443 for https
use TCP
web communication; HTTPS adds SSL/TLS encryption
Telnet
Port: 23
use TCP
remote access and transmit data in plaintext via cli
DNS
Port: 53
use UDP/TCP,UDP for queries, TCP for zone transfer
DNS is translating domain to IP. It follows a hierarchical process involving root, top-level domain(.com), and authoritative name server(google.com).
DNS workflow
- step: User start query: type www.google.com. client checks DNS cache in the browser; if not found, device checks DNS cache in OS.
- step: Device queries the recursive DNS server. Recursive DNS server(DNS resolver) first checks its DNS cache(rescursive call). if not found, DNS resolver start iterative query。
- step: DNS resolver fully queries(www.google.com) root DNS server. Root server point the server & responses with TLD server address for ‘.com’
- step: resolver fully queries(www.google.com) TLD server, TLD server responds with authoritative name server address for ‘google.com’
- step: resolver fully queries(www.google.com) the authoritative name server for a specific domain. Authoritative name server responds with an IP address. Authoritative server holds DNS records.
- step: resolver returns IP address to user’s device. Browser uses this iP to establish secure connection with the destination server via https.
DNS record
A 记录:
将域名映射到 IPv4 地址。
例如:www.google.com → 142.250.190.78。
AAAA 记录:
将域名映射到 IPv6 地址。
例如:www.google.com → 2607:f8b0:4005:809::2004。
CNAME 记录:
将域名映射到另一个域名(别名)。
例如:www.example.com → example.com。
NS 记录:
指定负责解析某个子域名的权威 DNS 服务器。
例如:example.com 的 NS 记录可能指向 ns1.example.com 和 ns2.example.com。
DHCP
Port: 67 for server,68 for client
use UDP
What is DHCP
DHCP isDynamic host configuration protocol. Dynamically assign client’s ip address and work on client-server model.
DHCP steps
- STEP DHCP DISCOVER PHRASE: DHCP client requesting ip with broadcast way(why ff because client don’t know which server)
- STEP DHCP OFFER PHRASE: DHCP server response with ff or unicast way
- STEP DHCP REQUEST PHRASE: ff way (client picked IP, tell others)
- STEP DHCP ACK PHRASE:ff or unicast way
2&4 step choose ff or unicast based on DHCP packet FLAG field: 0is unicast,1 ff.
DHCP snooping
happen in layer2. because DHCP client will send DHCH DISCOVER message in broadcast domain if it need assigned IP address. The unauthorized DHCP server assigns a malicious ip, leading to issues like
How to avoid:
Legitimate DHCP Server: Connected to GigabitEthernet0/1 (trusted port).
Rogue DHCP Server: Connected to GigabitEthernet0/2 (untrusted port).
Client: Connected to GigabitEthernet0/3 (untrusted port).
Steps:
- The client sends a DHCP DISCOVER message (broadcast).
- The legitimate DHCP server responds with a DHCP OFFER (allowed because it’s from a trusted port).
- The rogue DHCP server also responds with a DHCP OFFER (blocked because it’s from an untrusted port).
- Because did message filtering.The client receives only the legitimate DHCP OFFER and proceeds with the DHCP process.
Layer6: Presentation layer
Data translation and formatting:
Character encoding (ASCII, Unicode)
Data compression
Encryption/decryption (TLS/SSL)
Media formatting (JPEG, MPEG)
Layer5: Session layer
Manages communication/dialogue sessions:
Establishment (SYN)
Maintenance (keepalives)
Termination (FIN/RST)
Session recovery
Protocols: NetBIOS, RPC, PPTP
Layer4: Transport layer
segment transfer between port to port(process to process)
- TCP
reliable data transmission, 3-way handshake & 4-way handshake
It is a byte stream, each time data transfer have seq# and ack# to make sure data transfer is in order. TCP has accumulated acknowledgement, reliable connection, re-transmission, and congestion control. - UDP
unreliable data transfer, but fast so used in DNS query, VoIP
Layer3: Network layer
route data between hosts across different networks
- IP
used to define IP datagram(IP fragment MF=1, if DF=1 cannot fragment), packet size > MTU, ICMP error message. path of MTU discovery(ICMP+IP DFflag set) - NAT(SNAT,DNAT, PAT)
SNAT: many to one allows multiple devices behind NAT devices in private networks to share the same public IP and access the internet. DNAT: reverse of SNAT, one to many - ICMP
ping/traceroute - routing
RIP (distance vector)
OSPF (link-state advertisement)
BGP (path vector)
Layer2: Link layer
forwarding frame in one LAN
- Ethernet
MAC addressing, CSMA/CD, ethernet frame, frame format(EthernetII, 802.3) - ARP
IP<-> MAC mapping
ARP workflow: ARP cache, ARP request, ARP reply, update device’s MAC address - STP
prevent loop
Layer1: Physical layer
bit stream transmission
Key Elements
Media types (Copper, Fiber, Wireless)
Signaling methods
Topologies (Star, Bus, Ring)
Hardware (Hubs, NICs, Repeaters)
Standards (802.3, 802.11)Physical Layer Protocols
Ethernet (10/100/1000BASE-T)
DSL
SONET/SDH
802.11 PHY layer
