CyberSecurity covering prevention, detection, response, and risk management. It involves implementing security policies AAA(authentication, authorization, accountability), controls, and frameworks to ensure the (CIA triad)confidentiality, integrity, and availability of data and networks, while preventing DAD(discloure, alteration, and denial)
unauthorized access, compromise, destruction or denial of access.
Intro
- Confidentiality: data encryption, identity proofing, and two factor authentication
- Integrity: hash function or checksum
- Availability: able access to system or data. It can be achieved by maintaining equipment, performing hardware repairs, keeping OS and software up to date, and creating backups
Hats
- White hat attackers aim to discover security weaknesses so that they can be improved.
- Gray hat attackers are somewhere in between. While they may not have malicious intentions, they want to get something for their discovery.
- Black hat attackers take advantage of any vulnerabilities for illegal personal, financial or political gain.
Corporate Security practices
- Try the best to avoid human error via investing cybersecurity training, so they are aware of and able to spot a cyber attack
- Enfore two/multiple factor authentication to access files or app
- maintain log files and ongoing monitoring to identify anomalous behaviors that might indicate a data breach
- store password using a combination of salting and robust hash algoirthm
- separate cloud-based resources from the public internet into isolated private network segment
- grant employee access to internal system only via secure VPN connection
Malware
Spyware
Designed to track and spy on you, spyware monitors your online activity and can log every key you press on your keyboard, as well as capture almost any of your data, including sensitive personal information such as your online banking details. Spyware does this by modifying the security settings on your devices.
It often bundles itself with legitimate software or Trojan horses.
Adware
Adware is often installed with some versions of software and is designed to automatically deliver advertisements to a user, most often on a web browser. You know it when you see it! It’s hard to ignore when you’re faced with constant pop-up ads on your screen.
It is common for adware to come with spyware.
Backdoor
This type of malware is used to gain unauthorized access by bypassing the normal authentication procedures to access a system. As a result, hackers can gain remote access to resources within an application and issue remote system commands.
A backdoor works in the background and is difficult to detect.
Ransomware
This malware is designed to hold a computer system or the data it contains captive until a payment is made. Ransomware usually works by encrypting your data so that you can’t access it.
Some versions of ransomware can take advantage of specific system vulnerabilities to lock it down. Ransomware is often spread through phishing emails that encourage you to download a malicious attachment or through a software vulnerability.
Scareware
This is a type of malware that uses ‘scare’ tactics to trick you into taking a specific action. Scareware mainly consists of operating system style windows that pop up to warn you that your system is at risk and needs to run a specific program for it to return to normal operation.
If you agree to execute the specific program, your system will become infected with malware.
Rootkit
This malware is designed to modify the operating system to create a backdoor, which attackers can then use to access your computer remotely. Most rootkits take advantage of software vulnerabilities to gain access to resources that normally shouldn’t be accessible (privilege escalation) and modify system files.
Rootkits can also modify system forensics and monitoring tools, making them very hard to detect. In most cases, a computer infected by a rootkit has to be wiped and any required software reinstalled.
Virus
A virus is a type of computer program that, when executed, replicates and attaches itself to other executable files, such as a document, by inserting its own code. Most viruses require end-user interaction to initiate activation and can be written to act on a specific date or time.
Viruses can be relatively harmless, such as those that display a funny image. Or they can be destructive, such as those that modify or delete data.
Viruses can also be programmed to mutate in order to avoid detection. Most viruses are spread by USB drives, optical disks, network shares or email.
Trojan horse
This malware carries out malicious operations by masking its true intent. It might appear legitimate but is, in fact, very dangerous. Trojans exploit your user privileges and are most often found in image files, audio files or games.
Unlike viruses, Trojans do not self-replicate but act as a decoy to sneak malicious software past unsuspecting users.
Worms
This is a type of malware that replicates itself in order to spread from one computer to another. Unlike a virus, which requires a host program to run, worms can run by themselves. Other than the initial infection of the host, they do not require user participation and can spread very quickly over the network.
Worms share similar patterns: They exploit system vulnerabilities, they have a way to propagate themselves, and they all contain malicious code (payload) to cause damage to computer systems or networks.
Worms are responsible for some of the most devastating attacks on the Internet. In 2001, the Code Red worm had infected over 300,000 servers in just 19 hours.
Infiltration
DoS DDoS
The primary goal of DoS attack is to prevent target server from being able to handle additional requests.
A Distributed DoS (DDoS) attack is similar to a DoS attack but originates from multiple, coordinated sources. For example:
An attacker builds a network (botnet) of infected hosts called zombies, which are controlled by handler systems.
The zombie computers will constantly scan and infect more hosts, creating more and more zombies.
When ready, the hacker will instruct the handler systems to make the botnet of zombies carry out a DDoS attack.
Bonet
A bot computer is typically infected by visiting an unsafe website or opening an infected email attachment or infected media file. A botnet is a group of bots, connected through the Internet, that can be controlled by a malicious individual or group. Thousands of bots that are typically controlled through a command and control server.
These bots can be activated to distribute malware, launch DDoS attacks, distribute spam email, or execute brute-force password attacks. Cybercriminals will often rent out botnets to third parties for nefarious purposes.
On-Path Attacks
On-path attackers intercept or modify communications between two devices, such as a web browser and a web server, either to collect information from or to impersonate one of the devices.
This type of attack is also referred to as a man-in-the-middle.
SEO Poisoning
Attacker take advantage of popular search terms and use SEO to push malicious sites higher up the ranks of search results.
Exploits and Vulnerability
Buffer Overflow
Buffers are memory areas allocated to an application. A vulnerability occurs when data is written beyond the limits of a buffer. By changing data beyond the boundaries of a buffer, the application can access memory allocated to other processes. This can lead to a system crash or data compromise, or provide escalation of privileges.
Non-validated Input
Programs often require data input, but this incoming data could have malicious content, designed to force the program to behave in an unintended way.
For example, consider a program that receives an image for processing. A malicious user could craft an image file with invalid image dimensions. The maliciously crafted dimensions could force the program to allocate buffers of incorrect and unexpected sizes.
Race Conditions
This vulnerability describes a situation where the output of an event depends on ordered or timed outputs. A race condition becomes a source of vulnerability when the required ordered or timed events do not occur in the correct order or at the proper time.
Access Control Problems
Nearly all access controls and security practices can be overcome if an attacker has physical access to target equipment. For example, no matter the permission settings on a file, a hacker can bypass the operating system and read the data directly off the disk. Therefore, to protect the machine and the data it contains, physical access must be restricted, and encryption techniques must be used to protect data from being stolen or corrupted.
Security Appliances
Routers
Routers are primarily used to interconnect various network segments together, they usually also provide basic traffic filtering capabilities. This information can help you define which computer from a given network segment can commnunicate with which network segments.
Firewalls
Firewalls can look deeper into network traffic itself and identify malicioous behavior that has to be blocked. Firewalls can have sophisticated security policies applied to the traffic that is passing through them.
NAT Firewall
This firewall hides or masquerades the private addresses of network hosts. A small, internal local area network with computers requires access to the Internet using a single Internet connection.
Host-based Firewall
Filters ports and system service calls on a single computer operating system.
Proxy Server
Filters web content requests like URLs, domain names and media types.
Reverse Proxy Server
Placed in front of web servers, reverse proxy servers protect, hide, offload and distribute access to web servers.
Port Scanning
Port scanning is a process of probing a computer, server or other network host for open ports. It can be used maliciously as a reconnaissance tool to identify the operating system and services running on a computer or host, or it can be used harmlessly by a network administrator to verify network security policies on the network. Tool like Zenmap’s NMAP.
Intrusion Detection & Prevention Systems
IPS system use a set of traffic signatures that match and block malicious traffic and attacks.
IDS
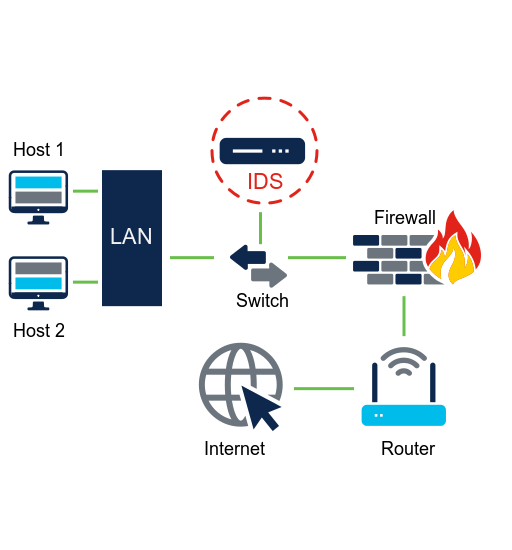 An IDS can either be a dedicated network device or one of serveral tools in a server, firewall or even a host computer OS, that scans data against a database of rules or attack signatures, looking for malicious traffic.
An IDS can either be a dedicated network device or one of serveral tools in a server, firewall or even a host computer OS, that scans data against a database of rules or attack signatures, looking for malicious traffic.
If a match is detected, IDS will log the detection and create an alert for a network administrator. It will not take action and therefore it will not prevent attacks from happening. The job of IDS is to detect, log and report.
The scanning performed by IDS slows down the network(known as latency). To prevent network delay, IDS is usually placed offline, separate from regular network traffic. Data is copied or mirrored by a switch and then forwarded to IDS for offline detection.
IPS
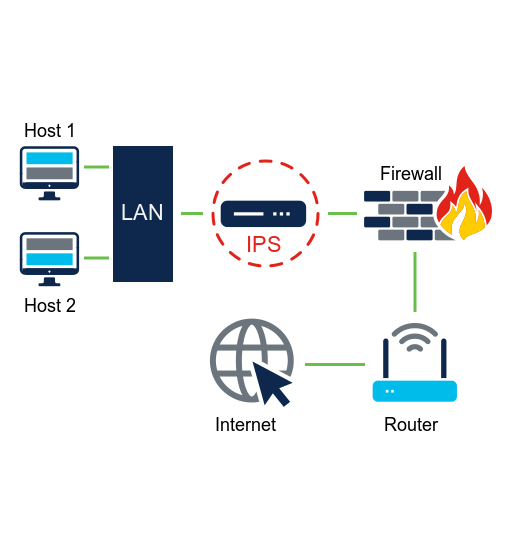 IPS can block or deny traffic based on a positive rule or signature match. One of the most well-known IPS/IDS system is Snort. Snort can perform real-time traffic and port analysis, logging, content searching and matching, as well as detect probes, attacks, and execute port scans. It also integrates with other third-party tools for reporting, performance and log analysis.
IPS can block or deny traffic based on a positive rule or signature match. One of the most well-known IPS/IDS system is Snort. Snort can perform real-time traffic and port analysis, logging, content searching and matching, as well as detect probes, attacks, and execute port scans. It also integrates with other third-party tools for reporting, performance and log analysis.
VPN
There are site-site VPN and site-point VPN.
IPSec VPN is site-site 🚇
- Uses IPSec (Internet Protocol Security) to create a secure tunnel between two networks (e.g., two office branches).
- IKE (Internet Key Exchange) is used to negotiate Security Associations (SA) and establish symmetric keys for data encryption.
- Asymmetric encryption (e.g., RSA, Diffie-Hellman) is used for key exchange.
- Symmetric encryption (e.g., AES, 3DES) is used for bulk data transfer (faster and more efficient).
SSL VPN is site-point 🏓
- Used by remote employees to securely access an organization’s network.
- Uses SSL/TLS handshake (same as HTTPS) for authentication and key exchange.
- Peer’s public key + own private key generate a session key (symmetric encryption for data transfer).
Antimalware or Antivirus
These systems use signatures or behavioral analysis of application to identify and block malicious code from being executed.
Real-time Detection
hackers are exploiting flaws in software before creators get a chance to fix them. When they do this, hackers are said to have carried out a zero-day attack and advanced persistent threats(APTs)!
Detecting attacks in real time requires actively scanning for attacks using firewall and IDS/IPS network devices. Next generation client and server malware detection with connections to online global threat centers must also be used. Today, active scanning devices and software must detect network anomalies using context-based analysis and behavior detection.
Behavior-based Security
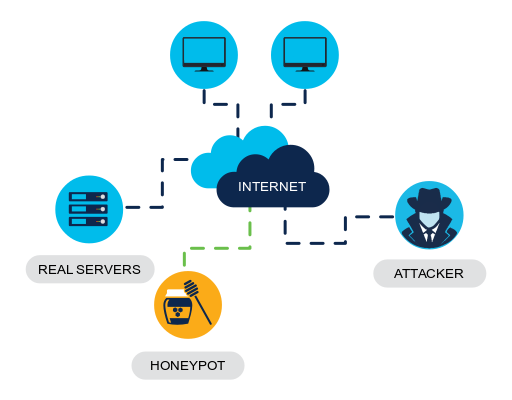
Honeypot
A honeyport is a behavior-based detection tool that lures the attacker in by appealing to their predicted pattern of malicious behavior. Once attacker is inside the honeypot, the network administrator can capture, loog and analyze their behavior so that they can build a better defense.
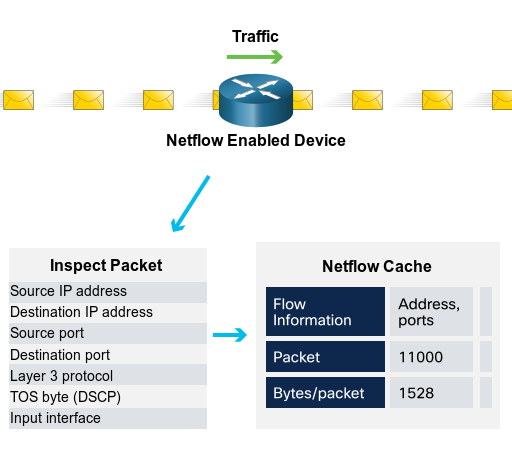
NetFlow
NetFlow technology is used to gather information about data flowing through a network, including who and what devices are in the network, and when and how users and devices access the network.
NetFlow is an important component in behavior-based detection and analysis. Switches, routers and firewalls equipped with NetFlow can report information about data entering, leaving and traveling through the network.
This information is sent to NetFlow collectors that collect, store and analyze NetFlow data, which can be used to establish baseline behaviors on more than 90 attributes, such as source and destination IP address.
Penetration Testing
Penetration testing, commonly known as pen testing, is the act of assessing a computer system, network or organization for security vulnerabilities. A pen test seeks to breach systems, people, processes and code to uncover vulnerabilities which could be exploited. This information is then used to improve the system’s defenses to ensure that it is better able to withstand cyber attacks in the future.
STEP: Planning
The pen tester gathers as much information as possible about a target system or network, its potential vulnerabilities and exploits to use against it. This involves conducting passive or active reconnaissance (footprinting) and vulnerability research.STEP: Scanning
The pen tester carries out active reconnaissance to probe a target system or network and identify potential weaknesses which, if exploited, could give an attacker access. Active reconnaissance may include:
- port scanning to identify potential access points into a target system
- vulnerability scanning to identify potential exploitable vulnerabilities of a particular target
- establishing an active connection to a target (enumeration) to identify the user account, system account and admin account.
- STEP: Gaining access
The pen tester will attempt to gain access to a target system and sniff network traffic, using various methods to exploit the system including:
- launching an exploit with a payload onto the system
- breaching physical barriers to assets
- social engineering
- exploiting website vulnerabilities
- exploiting software and hardware vulnerabilities or misconfigurations
- breaching access controls security
- cracking weak encrypted Wi-Fi.
STEP: Maintaining access
The pen tester will maintain access to the target to find out what data and systems are vulnerable to exploitation. It is important that they remain undetected, typically using backdoors, Trojan horses, rootkits and other covert channels to hide their presence.
When this infrastructure is in place, the pen tester will then proceed to gather the data that they consider valuable.STEP: Analysis and reporting
The pen tester will provide feedback via a report that recommends updates to products, policies and training to improve an organization’s security.
Incident Action
SIEM
A Security Information and Event Management (SIEM) system collects and analyzes security alerts, logs, and other real-time and historical data from security devices on the network to facilitate early detection of cyber attacks.
DLP
A Data Loss Prevention (DLP) system is designed to stop sensitive data from being stolen from or escaping a network. It monitors and protects data in three different states: data in use (data being accessed by a user), data in motion (data traveling through network) and data at rest (data stored in a computer network or device).
